Electronic health records (EHRs) are the future of the provider‐patient relationship. As the storage, retrieval and sharing of information via EHR accelerates, providers benefit from the most accurate and up‐to‐date information available. The delivery of care is optimized through these systems giving providers the information necessary to make the most effective clinical decisions for their patients.
Electronic health records (EHRs) are the future of the provider‐patient relationship. As the storage, retrieval and sharing of information via EHR accelerates, providers benefit from the most accurate and up‐to‐date information available. The delivery of care is optimized through these systems giving providers the information necessary to make the most effective clinical decisions for their patients.
The issue of patient security is an ongoing concern. Privacy of our medical data is one of the cornerstones of our healthcare system. This code of confidentiality empowers patients to share critical information with providers and, in turn, allows them to make the most appropriate diagnosis and plan of care necessary. In a recent blog entitled Living on a Cloud, we discussed how physical therapists are beginning to embrace ‘cloud computing’ as the new standard for accessing patient information any time and anywhere without having to purchase a server, upload a program or even back up their information. We emphasized that these services must provide Health Insurance Portability and Accountability Act (HIPAA) compliant user logins to ensure patient‐therapist confidentiality and should be SSL encrypted to the level required by CMS guidelines.
So, just as with our financial information we must ask the same questions concerning our patient data: Is this data vulnerable to internet attacks and security breaches? What precautions are providers taking to avoid these issues?
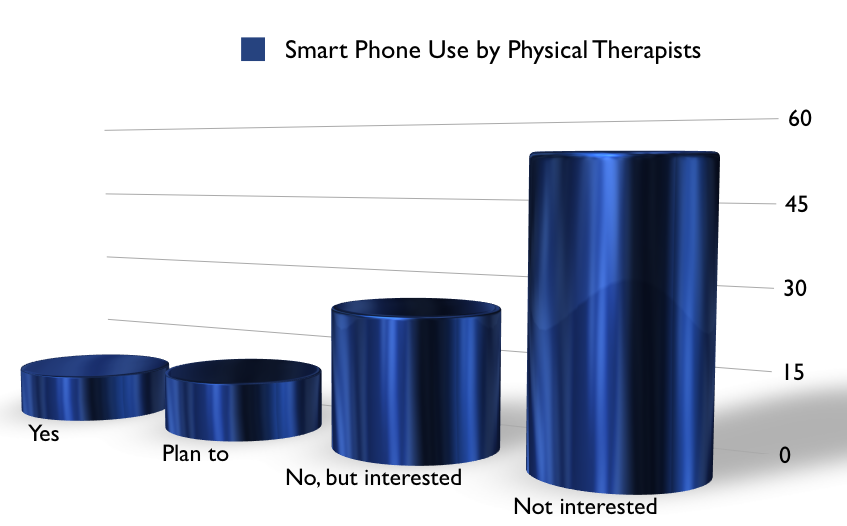
Here are some facts on EHR security. A recent study conducted by the consulting firm, Software Advice, found that security breaches of patient data through internet hacking only account for a small percentage (6%) of HIPAA violations (2, 3). A majority (63%) actually came from physical theft and unauthorized access or disclosure (16%). Of EHR violations, all involved on‐premise violations as opposed to ‘cloud based’ breaches. The author of the study points out that, “HIPAA violations aren’t happening in the cloud, rather, they’re happening in the doctor’s office, hospital IT closets, cars, subways, and homes.” In order to continue the safety of patient data, providers need to take precautions to comply with HIPAA Privacy, Security, and Breach Notification Rules (1). These include:
• Ensuring that any disclosure of patient information comply with HIPAA Privacy Rule
• Ensure the service performs a HIPAA Security Rule risk analysis indentifying potential threats and vulnerabilities to protected health information
• Ensure that service conforms to the HIPAA Breach Notification Rule which requires the reporting of breaches of protected health information
It is clear that EHRs can enhance the quality of patient care and that taking the necessary precautions to protect privacy is a crucial step to ensure that our healthcare system moves closer to a paperless practice model.
Resources
1. Dolan, B. 2011. Mobile Health: How to Comply with HIPAA, mobihealthnews, http://mobihealthnews.com/11272/mobile‐health‐how‐to‐comply‐with‐hipaa/.
2. Koploy, M. 2011. HHS Data Tells the True Story of HIPAA Violations in the Cloud, http://www.softwareadvice.com/articles/medical/hipaa‐violations‐arent‐in‐the‐cloud‐1062011/#ixzz1TYEUKe4G.
3. Simmons, j. 2011. Can ‘clouds’ protect patient data from security breaches?, FierceEMR, http://www.fierceemr.com/story/can‐clouds‐protect‐patient‐data‐security‐breaches/2011‐06‐23.
This guest post was co‐authored by Bronwyn Spira, P.T., President of Force Therapeutics and Mark Anthony Fields, Ph.D., M.P.H. Force Therapeutics can be found at www.forcetherapeutics.com, www.facebook.com/forcetherapeutics, or www.twitter.com/ForceTherEx.